How Quantum Cryptography Works: A Step-by-Step Guide
Oct 18, 2024



Nowadays, when data breaches and cyberattacks become more frequent the level of robust encryption techniques has also become higher. Despite their proven effectiveness, those cryptographic methods are more and more endangered by increasing computing power, especially with the emergence of quantum computing.
As an answer to these threats, Quantum Cryptography, a new technology that exploits quantum mechanics to establish unbreakable communication, is developed. One of the very important elements of quantum cryptography is Quantum Key Distribution which provides a reliable way of sending encryption keys that cannot be intercepted.
This article will talk about the vital issue of quantum cryptography, tell us what is a QKD, discuss its uses, and show how Decentrablock can help in its use.
Why is Quantum Cryptography Important?
Quantum cryptography is a next-level security protocol built to fix the weak spots of classical cryptography.
1. Security Threats from Quantum Computing: Traditional cryptography methods like RSA and ECC are based on the challenge of factorization of large numbers or the problem of discrete logarithms. But, quantum computers can use algorithms like Shor's which might be able to solve those problems much faster, to the point that these classical encryption methods will be considered obsolete.
2. Ultimate Security through Quantum Mechanics: Quantum cryptography is the science that makes use of quantum mechanics rather than traditional approaches to develop encryption methods that are theoretically impossible for an opposing party to crack. These systems are managed under the rule of physics, which indicates that if somebody tries to reach the key, then they modify the key resulting in the hanging of the communication.
QKD / Quantum Key Distribution (QKD)
QKD is a technique employed to independently distribute the encryption keys by two parties, to ensure that no hacker or unauthorized third party records or tampers the key exchange without it being detected.
When it comes to classical cryptography, key distribution has always been a weak link. The problem starts when the encryption keys are shared over insecure channels and can be intercepted. With the help of quantum mechanics key distribution which is the quantum key distribution this risk can be eliminated. Superposition and entanglement are the principles of quantum mechanics used by (QKD).
How Does QKD Work?
Now that we have a clear sense of why QKD is critical, let’s dissect the mechanics of its functionality.
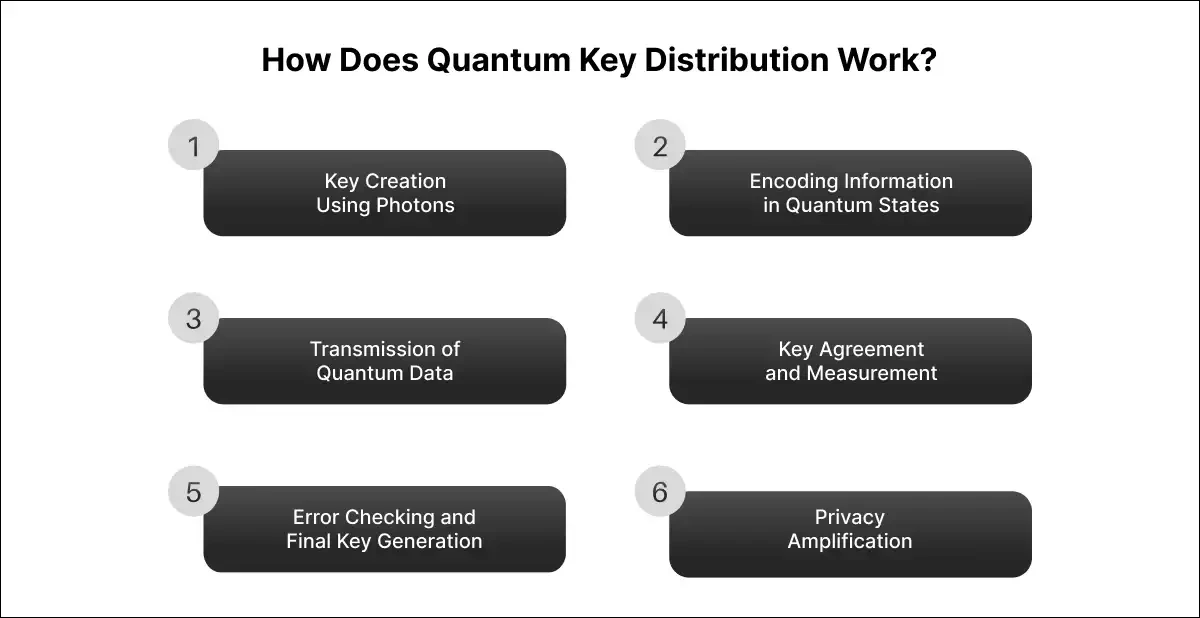
1. Key Creation Using Photons: In QKD, the encryption key is made with quantum particles, mainly photons. These photons are sent from one set of parties to another ( who are normally Alice and Bob) over a quantum channel.
2. Encoding Information in Quantum States: To ensure the safety of the key, the information is stored (encrypted) by transmitting photons. These quantum states, just as the classical computers use bits, can be symbolized as zeros or ones (0 or 1), but the active quantum mechanics will ensure extra security.
3. Transmission of Quantum Data: Alice sends the photon sequence to Bob. Each photon corresponds to one of the polarities or spasms that represent one bit of the encryption key. This process takes place over a quantum channel, which can be a fibre-optic cable or free space.
4. Key Agreement and Measurement: Bob gets the photons and assesses their states using a quantum key. As per the Heisenberg Uncertainty Principle, any effort by an unintended person (Eve) into the photogrammetry to get information will produce an error and alarm the system.
5. Error Checking and Final Key Generation: Once Bob has measured the states of the photons, Alice and Bob compare a subset of their key over a classical, insecure channel to check for errors. If too many discrepancies are detected, it indicates the presence of an eavesdropper, and the process is aborted. In case the key is mostly undeciphered, Alice and Bob continue with generating the final encryption key.
6. Privacy Amplification: When a slight difference is detected, Alice and Bob both make use of privacy amplification techniques to narrow down the encryption key to a small specific number, thus guaranteeing its safety.
By using quantum physics' laws, QKD gives a level of security that no classical system can achieve at the moment. In case someone tries to listen in on the quantum channel and will be exposed without detection of this, QKD is a perfect solution to secure communication in the quantum era.
Applications of QKD
Quantum Key Distribution is based on quantum physics, the application of which goes beyond the theory in the academic or mathematical field. Here are some actual QKD application areas:
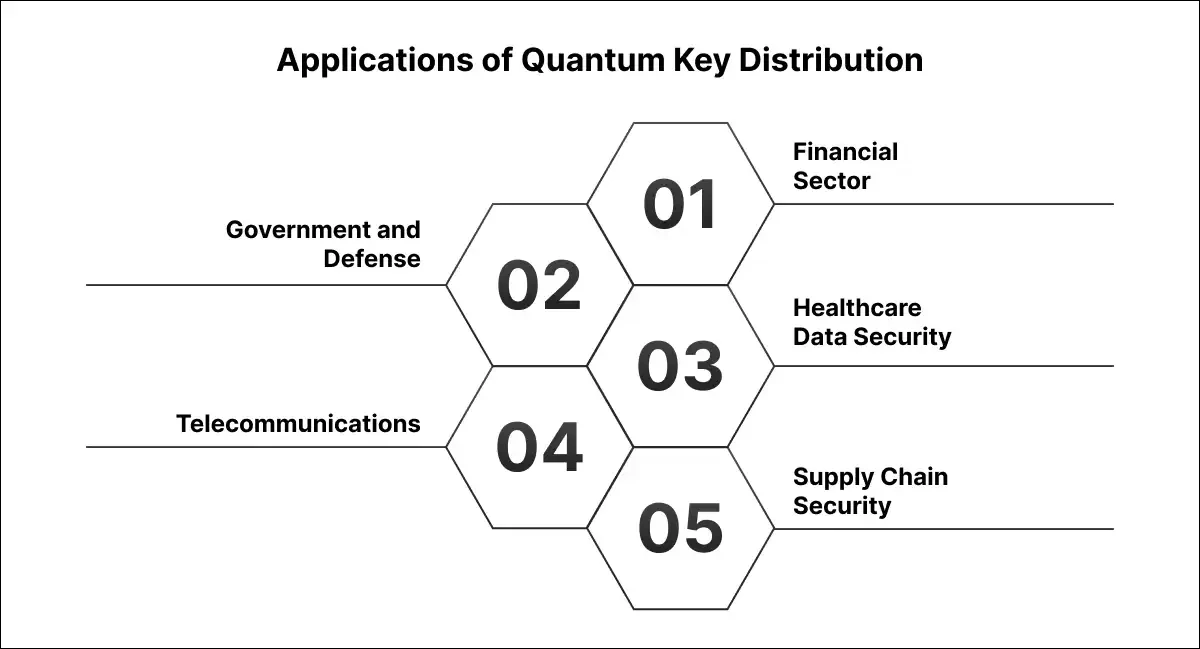
1. Financial Sector: The banks and financial institutions that transact through secure communication paths rely on the security of the communication lines. QKD can digitalize the security of these channels and thus the misuse of sensitive data including credit card numbers, transaction details, and financial reports remains confidential.
2. Government and Defense: National security agencies need communication systems with the highest protection against intelligence services. QKD technology can be equipped in secure networks to avoid espionage activity and the protection of classified information.
3. Healthcare Data Security: Medical facilities are in charge of vast personal data that all need proper defense. The use of quantum key distribution is the solution proposed for this since data breaches have been a major concern in the health sector.
4. Telecommunications: The companies gather new techniques and quantum communication developments, therefore the Quantum Key Distribution will enable them to offer their customers better and more secure services. This is because security and privacy will be the major concerns for these devices.
5. Supply Chain Security: Today, various industries, mainly manufacturing, logistics, and retail, rely increasingly on digital communications to govern their supply chains. Data security, thus, is most important. Quantum Key Distribution assists in the safeguarding of confidential supply chain data from cyber-attacks and industrial espionage.
Conclusion
Quantum cryptography is a secure communication technology that is going to define the future of secure communication. Because of the continuous development of quantum computing, the old encryption methods might not be efficient anymore. Businesses can protect themselves against cyber threats by using quantum cryptography, which guarantees the security of their data and communication systems in the future.
With the increasing demand for quantum-safe encryption, companies are looking for solutions that can be installed quickly in their existing infrastructure. Decentrablock is a professional organization that develops advanced cryptosystems that can then be implemented in various business types, including Quantum Key Distribution solutions.
Nowadays, when data breaches and cyberattacks become more frequent the level of robust encryption techniques has also become higher. Despite their proven effectiveness, those cryptographic methods are more and more endangered by increasing computing power, especially with the emergence of quantum computing.
As an answer to these threats, Quantum Cryptography, a new technology that exploits quantum mechanics to establish unbreakable communication, is developed. One of the very important elements of quantum cryptography is Quantum Key Distribution which provides a reliable way of sending encryption keys that cannot be intercepted.
This article will talk about the vital issue of quantum cryptography, tell us what is a QKD, discuss its uses, and show how Decentrablock can help in its use.
Why is Quantum Cryptography Important?
Quantum cryptography is a next-level security protocol built to fix the weak spots of classical cryptography.
1. Security Threats from Quantum Computing: Traditional cryptography methods like RSA and ECC are based on the challenge of factorization of large numbers or the problem of discrete logarithms. But, quantum computers can use algorithms like Shor's which might be able to solve those problems much faster, to the point that these classical encryption methods will be considered obsolete.
2. Ultimate Security through Quantum Mechanics: Quantum cryptography is the science that makes use of quantum mechanics rather than traditional approaches to develop encryption methods that are theoretically impossible for an opposing party to crack. These systems are managed under the rule of physics, which indicates that if somebody tries to reach the key, then they modify the key resulting in the hanging of the communication.
QKD / Quantum Key Distribution (QKD)
QKD is a technique employed to independently distribute the encryption keys by two parties, to ensure that no hacker or unauthorized third party records or tampers the key exchange without it being detected.
When it comes to classical cryptography, key distribution has always been a weak link. The problem starts when the encryption keys are shared over insecure channels and can be intercepted. With the help of quantum mechanics key distribution which is the quantum key distribution this risk can be eliminated. Superposition and entanglement are the principles of quantum mechanics used by (QKD).
How Does QKD Work?
Now that we have a clear sense of why QKD is critical, let’s dissect the mechanics of its functionality.

1. Key Creation Using Photons: In QKD, the encryption key is made with quantum particles, mainly photons. These photons are sent from one set of parties to another ( who are normally Alice and Bob) over a quantum channel.
2. Encoding Information in Quantum States: To ensure the safety of the key, the information is stored (encrypted) by transmitting photons. These quantum states, just as the classical computers use bits, can be symbolized as zeros or ones (0 or 1), but the active quantum mechanics will ensure extra security.
3. Transmission of Quantum Data: Alice sends the photon sequence to Bob. Each photon corresponds to one of the polarities or spasms that represent one bit of the encryption key. This process takes place over a quantum channel, which can be a fibre-optic cable or free space.
4. Key Agreement and Measurement: Bob gets the photons and assesses their states using a quantum key. As per the Heisenberg Uncertainty Principle, any effort by an unintended person (Eve) into the photogrammetry to get information will produce an error and alarm the system.
5. Error Checking and Final Key Generation: Once Bob has measured the states of the photons, Alice and Bob compare a subset of their key over a classical, insecure channel to check for errors. If too many discrepancies are detected, it indicates the presence of an eavesdropper, and the process is aborted. In case the key is mostly undeciphered, Alice and Bob continue with generating the final encryption key.
6. Privacy Amplification: When a slight difference is detected, Alice and Bob both make use of privacy amplification techniques to narrow down the encryption key to a small specific number, thus guaranteeing its safety.
By using quantum physics' laws, QKD gives a level of security that no classical system can achieve at the moment. In case someone tries to listen in on the quantum channel and will be exposed without detection of this, QKD is a perfect solution to secure communication in the quantum era.
Applications of QKD
Quantum Key Distribution is based on quantum physics, the application of which goes beyond the theory in the academic or mathematical field. Here are some actual QKD application areas:

1. Financial Sector: The banks and financial institutions that transact through secure communication paths rely on the security of the communication lines. QKD can digitalize the security of these channels and thus the misuse of sensitive data including credit card numbers, transaction details, and financial reports remains confidential.
2. Government and Defense: National security agencies need communication systems with the highest protection against intelligence services. QKD technology can be equipped in secure networks to avoid espionage activity and the protection of classified information.
3. Healthcare Data Security: Medical facilities are in charge of vast personal data that all need proper defense. The use of quantum key distribution is the solution proposed for this since data breaches have been a major concern in the health sector.
4. Telecommunications: The companies gather new techniques and quantum communication developments, therefore the Quantum Key Distribution will enable them to offer their customers better and more secure services. This is because security and privacy will be the major concerns for these devices.
5. Supply Chain Security: Today, various industries, mainly manufacturing, logistics, and retail, rely increasingly on digital communications to govern their supply chains. Data security, thus, is most important. Quantum Key Distribution assists in the safeguarding of confidential supply chain data from cyber-attacks and industrial espionage.
Conclusion
Quantum cryptography is a secure communication technology that is going to define the future of secure communication. Because of the continuous development of quantum computing, the old encryption methods might not be efficient anymore. Businesses can protect themselves against cyber threats by using quantum cryptography, which guarantees the security of their data and communication systems in the future.
With the increasing demand for quantum-safe encryption, companies are looking for solutions that can be installed quickly in their existing infrastructure. Decentrablock is a professional organization that develops advanced cryptosystems that can then be implemented in various business types, including Quantum Key Distribution solutions.
Nowadays, when data breaches and cyberattacks become more frequent the level of robust encryption techniques has also become higher. Despite their proven effectiveness, those cryptographic methods are more and more endangered by increasing computing power, especially with the emergence of quantum computing.
As an answer to these threats, Quantum Cryptography, a new technology that exploits quantum mechanics to establish unbreakable communication, is developed. One of the very important elements of quantum cryptography is Quantum Key Distribution which provides a reliable way of sending encryption keys that cannot be intercepted.
This article will talk about the vital issue of quantum cryptography, tell us what is a QKD, discuss its uses, and show how Decentrablock can help in its use.
Why is Quantum Cryptography Important?
Quantum cryptography is a next-level security protocol built to fix the weak spots of classical cryptography.
1. Security Threats from Quantum Computing: Traditional cryptography methods like RSA and ECC are based on the challenge of factorization of large numbers or the problem of discrete logarithms. But, quantum computers can use algorithms like Shor's which might be able to solve those problems much faster, to the point that these classical encryption methods will be considered obsolete.
2. Ultimate Security through Quantum Mechanics: Quantum cryptography is the science that makes use of quantum mechanics rather than traditional approaches to develop encryption methods that are theoretically impossible for an opposing party to crack. These systems are managed under the rule of physics, which indicates that if somebody tries to reach the key, then they modify the key resulting in the hanging of the communication.
QKD / Quantum Key Distribution (QKD)
QKD is a technique employed to independently distribute the encryption keys by two parties, to ensure that no hacker or unauthorized third party records or tampers the key exchange without it being detected.
When it comes to classical cryptography, key distribution has always been a weak link. The problem starts when the encryption keys are shared over insecure channels and can be intercepted. With the help of quantum mechanics key distribution which is the quantum key distribution this risk can be eliminated. Superposition and entanglement are the principles of quantum mechanics used by (QKD).
How Does QKD Work?
Now that we have a clear sense of why QKD is critical, let’s dissect the mechanics of its functionality.

1. Key Creation Using Photons: In QKD, the encryption key is made with quantum particles, mainly photons. These photons are sent from one set of parties to another ( who are normally Alice and Bob) over a quantum channel.
2. Encoding Information in Quantum States: To ensure the safety of the key, the information is stored (encrypted) by transmitting photons. These quantum states, just as the classical computers use bits, can be symbolized as zeros or ones (0 or 1), but the active quantum mechanics will ensure extra security.
3. Transmission of Quantum Data: Alice sends the photon sequence to Bob. Each photon corresponds to one of the polarities or spasms that represent one bit of the encryption key. This process takes place over a quantum channel, which can be a fibre-optic cable or free space.
4. Key Agreement and Measurement: Bob gets the photons and assesses their states using a quantum key. As per the Heisenberg Uncertainty Principle, any effort by an unintended person (Eve) into the photogrammetry to get information will produce an error and alarm the system.
5. Error Checking and Final Key Generation: Once Bob has measured the states of the photons, Alice and Bob compare a subset of their key over a classical, insecure channel to check for errors. If too many discrepancies are detected, it indicates the presence of an eavesdropper, and the process is aborted. In case the key is mostly undeciphered, Alice and Bob continue with generating the final encryption key.
6. Privacy Amplification: When a slight difference is detected, Alice and Bob both make use of privacy amplification techniques to narrow down the encryption key to a small specific number, thus guaranteeing its safety.
By using quantum physics' laws, QKD gives a level of security that no classical system can achieve at the moment. In case someone tries to listen in on the quantum channel and will be exposed without detection of this, QKD is a perfect solution to secure communication in the quantum era.
Applications of QKD
Quantum Key Distribution is based on quantum physics, the application of which goes beyond the theory in the academic or mathematical field. Here are some actual QKD application areas:

1. Financial Sector: The banks and financial institutions that transact through secure communication paths rely on the security of the communication lines. QKD can digitalize the security of these channels and thus the misuse of sensitive data including credit card numbers, transaction details, and financial reports remains confidential.
2. Government and Defense: National security agencies need communication systems with the highest protection against intelligence services. QKD technology can be equipped in secure networks to avoid espionage activity and the protection of classified information.
3. Healthcare Data Security: Medical facilities are in charge of vast personal data that all need proper defense. The use of quantum key distribution is the solution proposed for this since data breaches have been a major concern in the health sector.
4. Telecommunications: The companies gather new techniques and quantum communication developments, therefore the Quantum Key Distribution will enable them to offer their customers better and more secure services. This is because security and privacy will be the major concerns for these devices.
5. Supply Chain Security: Today, various industries, mainly manufacturing, logistics, and retail, rely increasingly on digital communications to govern their supply chains. Data security, thus, is most important. Quantum Key Distribution assists in the safeguarding of confidential supply chain data from cyber-attacks and industrial espionage.
Conclusion
Quantum cryptography is a secure communication technology that is going to define the future of secure communication. Because of the continuous development of quantum computing, the old encryption methods might not be efficient anymore. Businesses can protect themselves against cyber threats by using quantum cryptography, which guarantees the security of their data and communication systems in the future.
With the increasing demand for quantum-safe encryption, companies are looking for solutions that can be installed quickly in their existing infrastructure. Decentrablock is a professional organization that develops advanced cryptosystems that can then be implemented in various business types, including Quantum Key Distribution solutions.

DecentraBlock is at the forefront of blockchain innovation, revolutionizing how businesses secure, transact, and grow in the digital age. Join us on a journey to harness the full potential of decentralized technology for a more efficient and transparent future.
Services
Subscribe to Our Newsletter
Get the latest news, updates, and insights on blockchain technology directly to your inbox. Sign up for our newsletter today!
© 2024 DecentraBlock. All rights reserved.

DecentraBlock is at the forefront of blockchain innovation, revolutionizing how businesses secure, transact, and grow in the digital age. Join us on a journey to harness the full potential of decentralized technology for a more efficient and transparent future.
Services
Subscribe to Our Newsletter
Get the latest news, updates, and insights on blockchain technology directly to your inbox. Sign up for our newsletter today!
© 2024 DecentraBlock. All rights reserved.

DecentraBlock is at the forefront of blockchain innovation, revolutionizing how businesses secure, transact, and grow in the digital age. Join us on a journey to harness the full potential of decentralized technology for a more efficient and transparent future.
Services
Subscribe to Our Newsletter
Get the latest news, updates, and insights on blockchain technology directly to your inbox. Sign up for our newsletter today!
© 2024 DecentraBlock. All rights reserved.


